Juju Support for Google Cloud Platform
Udi Nachmany
on 3 June 2015
 As you may have noticed in our release notes, the recent release of a stable 1.23.2 Juju core (and its 1.23.3 follow-on) is packed with goodies such as support for systemd (and Vivid), improved proxy support for restrictive networks, new charm actions, as well as a first run at Juju service leader elections – and the list goes on!
As you may have noticed in our release notes, the recent release of a stable 1.23.2 Juju core (and its 1.23.3 follow-on) is packed with goodies such as support for systemd (and Vivid), improved proxy support for restrictive networks, new charm actions, as well as a first run at Juju service leader elections – and the list goes on!
For public cloud users of Ubuntu, we are particularly excited to let you know that this version includes support for Google Compute Engine (GCE). If you’re a Google Cloud Platform user, you can now spin up, scale, and modify production workloads easily and quickly, with our market-leading, open source universal modelling tool, Juju. If you are already a Juju user and thinking about using Google Cloud Platform, you can take your magic over to them and get going in no time.
Configuring for GCE: https://jujucharms.com/docs/stable/config-gce
Juju 1.23.2 release notes: https://jujucharms.com/docs/devel/reference-release-notes
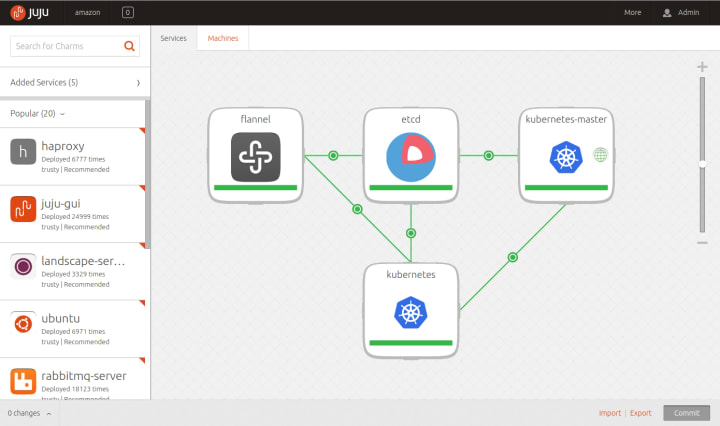
This ties in very nicely to the upstream work (here and here) we’ve been doing in the past months, to make it easy to deploy Kubernetes servers using Juju, even on cloud environments that are not yet supported by the Kubernetes project.
On a related note, if you’re using Google Cloud Platform you’ve probably taken a look at the sleek Cloud Launcher Google have released recently. And if you looked closely, you also noticed that you can now spin up your Ubuntu VMs using this very friendly UI.
 And at the time of writing, since the list is sorted by popularity, Ubuntu (unsurprisingly) has four of the top six spots.
And at the time of writing, since the list is sorted by popularity, Ubuntu (unsurprisingly) has four of the top six spots.
Ubuntu cloud
Ubuntu offers all the training, software infrastructure, tools, services and support you need for your public and private clouds.
Newsletter signup
Related posts
A deep dive into our grid system and typography for the A4 format
We recently redesigned our whitepapers as part of our broader rebranding project. Let’s look at some of the ideas behind our approach to layout and...
How Ubuntu Pro + Support keeps your Ubuntu 20.04 LTS secure and stable
Running Ubuntu 20.04 LTS with ESM keeps your systems up to date with essential security patches. But when something breaks or a complex issue arises, Ubuntu...
7 considerations when building your ML architecture
As the number of organizations moving their ML projects to production is growing, the need to build reliable, scalable architecture has become a more pressing...
